How big a disaster will it be if your Facebook account gets hacked? What will you lose when your laptop’s hard drive self-destructs? How will you cope if you lose your mobile phone?
The digital world provides a wealth of applications for business and pleasure. We generate huge numbers of files including our work, our money, our photos and videos – a comprehensive archive of our modern lives. These digital assets are hugely important and need protecting.
Don’t have a Digital Crisis Management Plan?
Well, there are two options:
- We create one today, or
- We wait until it’s too late…
There are two principle theatres for digital disasters; system failure and criminal intervention.
File not found
Computers and mobile phones are disposable but our data is not. The fridge in your kitchen has been switched on doing its job seamlessly for the last decade. How many laptops and mobile phones have you got through in that time?
Your important data should not be stored locally on a single device. It is easy to synchronise all your devices through cloud services so that you can access your contacts, calendar and files from any device at any time. Syncing via the cloud is free and easy.
Google and Apple both provide free cloud storage as do Amazon and Dropbox. Software is available that carries out incremental backups both to external and off-site drives automatically – meaning you don’t have to remember to do it.
If you have a lot of important data (like we do) then there are dedicated, unlimited storage services providing backup-and-restore facilities from around $9 a month.
External hard drives are ten-a-penny, tiny, capacious and stable. For the price of a night out, you can buy a solid-state hard drive which will take years to fill. Flash drives and SSD drives are subtly different but the important thing is that they have no moving parts. Short of chiselling it into slabs of marble, there’s no more enduring way to store your data.
Checklist
- Sync your contacts, calendar and important files through cloud services;
- Keep regular backups of your documents on external hard drives, and
- Back up your documents to off-site data storage.
That’s our Digital Crisis Management Plan in place in the event of a catastrophic coffee spillage on our laptop. Oh, but all our passwords are saved in our browser! But that’s ok because we use our first pet’s maiden name for everything…
Pa$$words and Two-Factor Authentication
Don’t use the same password in multiple logins. Do we really have to say this? The most common form of data breach is in the vast databases of big service providers. Amazon, AirBnB, Facebook, Instagram, Netflix, eBay… anywhere you have a login, there’s a database holding your data which is a target for hackers.

LinkedIn was hacked in June 2021 and the data of 700 million of its users posted for sale on the dark web. That was 92% of its users’ data compromised
The hackers harvest and collate your personal data and sell it in vast troves on the dark web. You won’t know about it until you start getting bills for a mobile phone you never bought on a credit card you don’t own.
The bad news is there is nothing we can do to prevent these data breaches but there are measures we can take to mitigate.
Firstly, use big random passwords generated and managed for you by a password manager. There are plenty to choose from. In the Graphic Violence office, we use LastPass and Bitwarden – using one as backup of the other. Both have apps for use on mobile devices.

The most recent Facebook data breach happened in April 2021, when the personal data of 533 million users was made freely available on a public forum. Facebook was the single most hacked network in 2021
Storing your passwords in your browser on your laptop is not a useful solution. The data is local to your device and when it dies on you (it will), you’ve lost all your logins. Password managers are cloud-based services you can access from any device.
Checklist
- Create a password manager account;
- Set a unique and complex password on each of your logins, and
- Activate Two-Factor Authentication where available.
Increasingly, security services are being consolidated by providers. Many companies who offer Virtual Private Networks (VPN) include dark web monitoring to see if your email address has appeared in a data breach, password management, and malware detection for desktop and mobile devices. VPN providers protect multiple devices with a single plan.
Activate Two-Factor Authentication (2FA) on your accounts and then your passwords are of limited use to the hackers without access to your mobile phone. But there are complications.

In January 2023, X-Twitter was hacked and more than 220 million users’ email address details were put up for sale on the dark web when the social network refused to pay a ransom
Many 2FAs involve a verification code sent by SMS to your mobile phone. This is not very useful if you have no phone signal (we’ve been there) or worse still, if you’ve lost your phone.
Authenticator apps on mobile devices provide 2FA security to your other apps like Facebook and Instagram but do it such that you can transfer to a new phone, via web browser, without needing access to the old device. They also allow you to add 2FA without the need to disclose your phone number. For example, you can add 2FA to Facebook on your mobile without needing to give Facebook your phone number.
Mobile phones are vulnerable not simply because they are easily lost or damaged but also because of exposure to public wi-fi networks. VPN services protect your mobile on public wi-fi and a host of apps are available to protect against malware and viruses.

In 2021, an unprotected database on Instagram allowed access to over 214 million user accounts without so much as a password. This exposed email addresses, contact numbers, locations, and biodata
Google and Apple both provide free authenticator services with find my phone and remote disable / delete functions in the event of your phone being lost or stolen.
Checklist
- Protect your devices with VPN;
- Protect your phone with anti-malware app;
- Activate find / delete mobile phone function, and
- Install a 2FA app on your mobile devices.
Faking and entering
‘Phishing’ is the practice of harvesting personal data with fake login pages. Typically, a message or email advises you your account has been disabled or is going to be deleted because of a T&Cs violation, suspicious activity or the need to verify something or other.
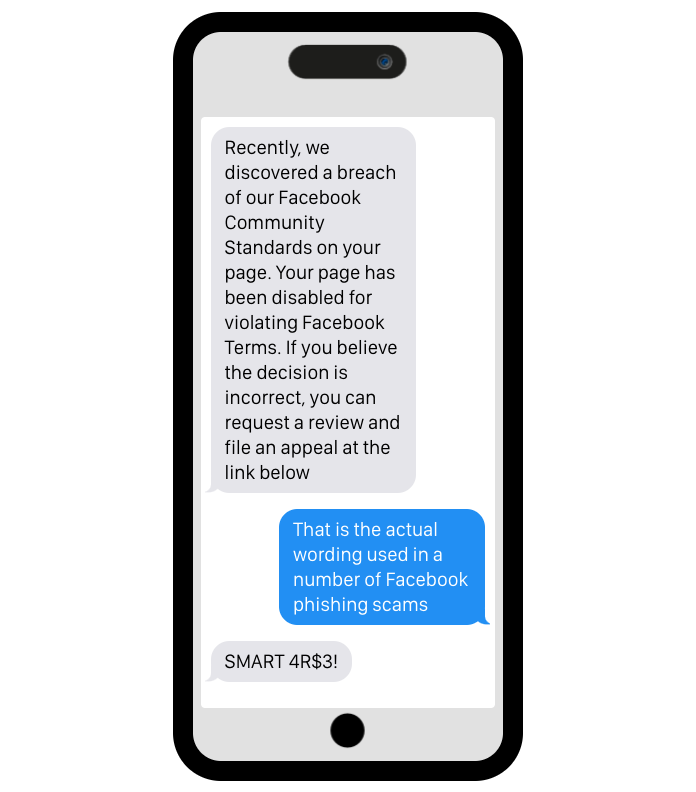
A link is provided for you to carry out the required action and instructs you to login again, for security. It’s a fake login page. You enter your details and continue on your way without realising you’ve just handed over your email and or phone number and password to the hackers.
They now have access to your Facebook account and will change the password and lock you out. If you have made purchases through Facebook, they’ll have access to your payment details too. Masquerading as you, they’ll now brag about the easy money you are making on cryptocurrency. They’ll post links to more scams and your friends will fall for them because they trust your recommendations.
These phishing scams target personal and business profiles across all online accounts including Instagram, X-Twitter, LinkedIn, PayPal, Gmail et al. Recovering a hacked account is entirely dependent on the service provider and is, by no means, a certainty.
Spot the scams
Always be sceptical of messages. Copy the text of the message and post it into a Google search. The first result will tell you whether it is a scam or not.
The golden rule is never use the link provided. If your PayPal account has been suspended, you’ll find that out by signing in via paypal.com.
The scammer’s fake login page always looks very convincing but it won’t have the real URL. Password managers spot this and won’t offer up your login details. We know, our password manager saved us on a fake Gmail login once.
Do it today
If you do nothing else today to ramp up your digital security, change the passwords on the accounts most important to you. If you are still using the same login for your Facebook and LinkedIn accounts you set when you created them, then your details are definitely out there in multiple data breaches.
We hope this article raises your awareness of the likely vulnerabilities in your digital life and prompts you to increase your security. It is a huge subject and below is a list of links you’ll find useful for more guidance but if you aren’t interested in reading any more but want some barricades errecting, call or message us.
Read more
- The Best Cloud Storage and File-Sharing Services for 2024 – PC Mag
- Best Cloud Backup Services 2024: Free & Cheap Backup Storage – Cloudwards
- The 72 Biggest Data Breaches of All Time [Updated 2024] – UpGuard
- Facebook Data Breaches: Full Timeline Through 2023 – Firewall Times
- Which of Your Social Media Accounts is Most Likely to Get Hacked? – Digit News
- The Best Security Suites for 2024 – PC Mag
- Best free and paid-for mobile antivirus apps – Which?
- Find, lock, or erase your lost Android device – Google Help
- Find your lost iPhone or iPad with Find My – Apple Support
- The best VPN service in 2024 – Tech Radar
- Check if your email address is in a data breach – Have I Been Pwned?
- The Best Password Managers for 2024 – PC Mag

